Phone:
(678) 951-0626
Physical address:
4575 Webb Bridge Rd.
Suite #4345
Alpharetta, Georgia 30023

Using NFC (Near Field Communication) tags with security guards can be an efficient way to enhance security measures and streamline operations. Here’s a step-by-step guide on how to use NFC tags effectively:
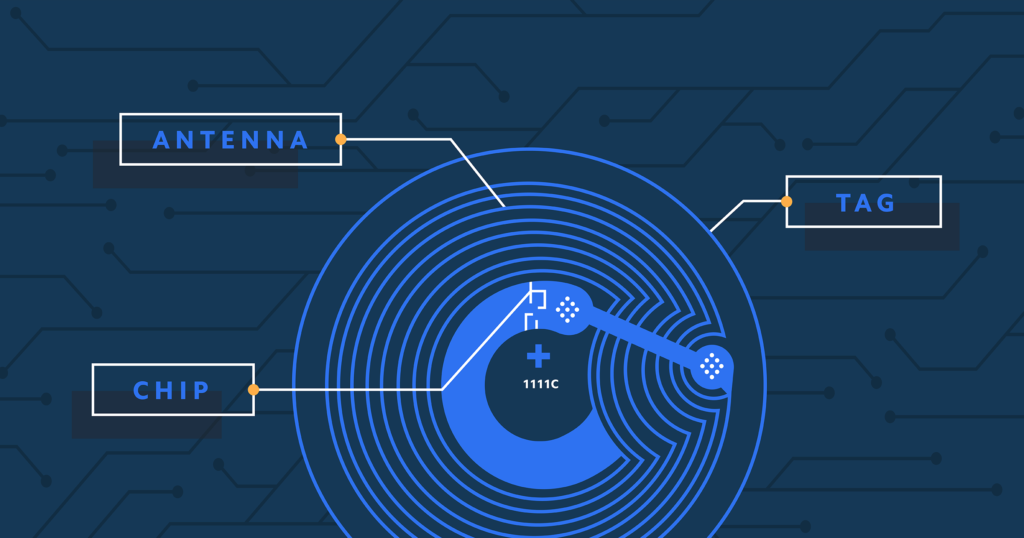
NFC is a short-range wireless communication technology that enables the exchange of data between devices nearby. NFC tags contain embedded information that can be read by NFC-enabled devices, such as smartphones or specialized NFC readers. Learn more on NFC| Near Field Communication Security Basics.
Identify specific scenarios where NFC tags can be beneficial for security guards and boost efficiency. For example, you can use NFC tags to track patrols, verify checkpoints, access important information, data field requirements (i.e. temperature checks) with restricted input range, or log incidents. Another efficiency booster is a security feature called remote guarding. Remote Guarding allows the front gate operations to be run and monitored remotely by an internal or external remote guard company through a gate kiosk such as TEKWave Solutions AllBox. Allowing a physical guard to be free to patrol the property.
Select NFC tags that suit your requirements. There are various types of NFC tags available, including adhesive stickers, keychains, cards, or even wearable options. Ensure they are compatible with the NFC technology supported by the devices used by your security guards.
Use an NFC-enabled device (such as a smartphone or tablet)with the necessary apps or software to program the information onto the NFC tags. This could include patrol routes, checkpoints, incident reporting forms, emergency contact details, or any other relevant data. NFC tags can be used to trigger other devices such as lights or sensors when a guard is securing an area. Also, you can program the NFC tags to set off alarms or timer reminders for the guards. Programming the NFC tags correctly can implement additional layers of security to confirm the property is secured.

Place the NFC tags strategically at various locations within the premises that require monitoring or verification. These can be at key checkpoints, access points, or any other relevant areas that security guards need to interact with regularly.
Provide comprehensive training to security guards on how to use NFC-enabled devices to read and interact with the NFC tags. Educate them on the purpose and functionality of the tags, how to log data, and any specific procedures associated with NFC tag usage.
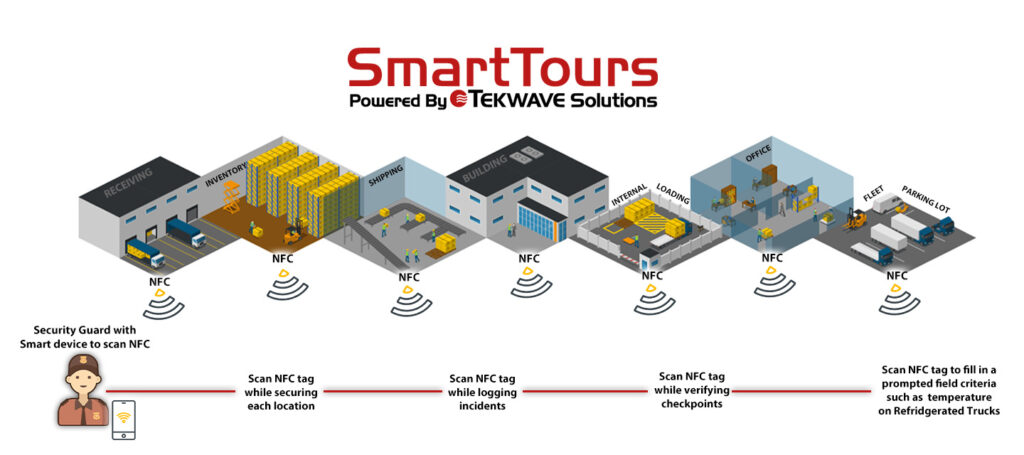
During their patrols, security guards can use their NFC-enabled devices to scan the NFC tags placed at designated checkpoints. The tags can be programmed to record the time, date, and identity of the security guard, providing an electronic log of the patrols. Research security guard management software such as TEKControl that digitally tracks and records the patrols. TEKWave has an NFC tag patrol product called SmartTours, which improves guards’ efficiency, and gives companies visibility on guard performance analytics.

Example of a security patrol route using NFC technology
NFC tags can also be used to store critical information, such as emergency procedures, maps, or incident reporting forms. Security guards can tap their NFC-enabled devices on the tags to quickly access the relevant information when needed.
If an incident occurs, security guards can use NFC tags to initiate incident reports by tapping their devices on specially programmed tags. This can streamline the reporting process and ensure accurate and timely documentation. Make sure to pair this with a guard management system or visitor management system such as TEKControl powered by TEKWave Solutions which keeps digital vaults of documentation while monitoring and logging the daily guard activities.
The information collected through NFC tags can be analyzed to identify patterns, monitor security guard performance, or assess areas that may require additional attention. This can aid in improving security protocols and making informed decisions.
Remember, security guards should always follow their organization’s policies and procedures when utilizing NFC tags and handling security-related tasks.
To learn more about NFC and other security-related technology, contact a specialist by clicking the link below.