Phone:
(678) 951-0626
Physical address:
4575 Webb Bridge Rd.
Suite #4345
Alpharetta, Georgia 30023

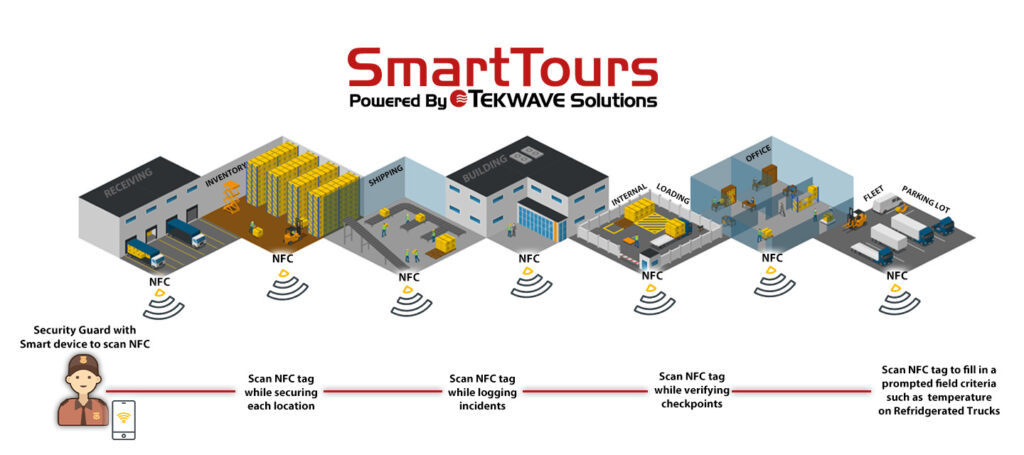
Using NFC (Near Field Communication) tags with security guards can greatly improve security measures and streamline operations within commercial, industrial or residential environments. With NFC technology, which allows for the exchange of data between nearby devices, these programmable tags can be read by NFC-enabled devices like smartphones or specialized NFC readers. By understanding NFC technology and identifying specific use cases, security guards can track patrols, verify checkpoints, access important information, and log incidents more efficiently. Additionally, a security feature called remote guarding enables front gate operations to be monitored and managed remotely, freeing up physical guards to patrol the property. By incorporating NFC programmable tags into their security protocols, security guards can enhance their effectiveness and efficiency in protecting their premises.
NFC, or Near Field Communication, is a short-range wireless communication technology that allows the exchange of data between devices in close proximity. It operates on radio frequency identification (RFID) technology and enables contactless communication between two NFC-enabled devices.
NFC works by establishing a connection when two devices are brought close together, typically within a few centimeters. One device acts as an initiator, generating a radio frequency field that allows the other device to respond and exchange data. This communication is initiated by tapping or bringing the devices close to each other.
NFC technology uses two modes of operation: active and passive. In passive mode, one device generates the radio frequency field and the other device responds to it. In active mode, both devices generate their own radio frequency fields, enabling bidirectional communication.
Using NFC technology offers numerous benefits, particularly in the context of security and efficiency. Some key advantages include:
NFC tags can be used to track the movements and patrols of security guards in commercial, industrial or residential environments. By placing NFC tags at various checkpoints or predetermined locations, guards can tap their NFC-enabled devices on the tags to register their presence. This provides a clear record of their patrols and ensures accountability.
Security guards often have to visit and verify multiple checkpoints or access points during their shifts. NFC tags can simplify this process by allowing guards to tap their devices on the designated tags to confirm their arrival and ensure that the checkpoint has been properly inspected. This reduces the margin for error and enhances overall security measures.
NFC tags can be programmed to store important information, such as emergency protocols, operating procedures, or contact details. Security guards can simply tap their devices on the corresponding tags to instantly access this information when needed, ensuring they have the necessary resources at their fingertips.
When incidents occur, it’s crucial to document and log relevant details for later investigation or reporting. NFC tags can be placed at incident-prone areas, and security guards can tap their devices on these tags to log relevant information, such as date, time, location, and incident details. This facilitates accurate incident reporting and ensures a comprehensive record of incidents.
With the help of NFC technology, security guards can carry out remote guarding operations more effectively. By installing NFC-enabled devices or readers at remote locations, guards can remotely monitor and control access to these areas. This allows them to provide real-time security oversight without physically being present, greatly improving the overall efficiency and coverage of their operations.
TEKWave Solutions aims to provide comprehensive vehicle access control solutions for gated properties. With their innovative technology and expertise, they ensure that only authorized vehicles can enter and exit these spaces, enhancing security and safety.
TEKWave Solutions focuses on securing and safeguarding mission-critical operations in various sectors, including distribution centers, gated HOAs (Homeowners Associations), and unmanned critical infrastructure. By implementing their security solutions, TEKWave ensures that these operations remain protected from potential threats.
TEKWave Solutions is committed to offering security solutions that not only enhance safety and security but also ensure compliance with relevant regulations and standards. They understand the importance of maintaining a secure and compliant environment for businesses and communities alike.
By utilizing NFC programable tags, security guards can significantly enhance security measures. These tags can be integrated into access control systems, allowing guards to verify checkpoints, track patrols, and ensure only authorized personnel have access to restricted areas.
NFC programable tags streamline security operations by automating various tasks. Instead of relying on manual processes, guards can simply tap their NFC-enabled devices on the tags to perform actions such as logging incidents, accessing important information, or verifying checkpoints. This reduces the time and effort required, enabling guards to focus on more critical tasks.
NFC programable tags facilitate efficient data exchange between devices. By storing relevant information in the tags, guards can quickly retrieve or update data by simply tapping their devices on the tags. This eliminates the need for manual data entry or paperwork, reducing the chances of errors and improving overall efficiency.
One of the key advantages of NFC programable tags is their compatibility with NFC-enabled devices, such as smartphones or specialized NFC readers. With the widespread use of these devices, implementing NFC technology becomes more accessible and cost-effective. Security guards can leverage their existing devices to tap and interact with NFC tags seamlessly.
Before starting to use NFC programable tags, it’s essential to understand their capabilities and limitations. Familiarize yourself with the technology, including how NFC works, what type of data can be stored in tags, and how they can be programmed.
Identify specific use cases where NFC programable tags can benefit security guards and improve operations. Consider scenarios such as tracking patrols, verifying checkpoints, accessing important information, logging incidents, or implementing remote guarding. Tailor the use cases to the specific needs of your security operations.
To fully utilize NFC programable tags, they need to be programmed with the desired information or actions. This can be done using specialized software or apps that allow you to configure the tags according to your requirements. The programming process may involve defining data fields, assigning actions, or encrypting the information stored in the tags.
After programming the NFC tags, it’s crucial to test their functionality and ensure they work as intended. Conduct thorough testing by tapping the NFC-enabled devices on the tags and verifying that the expected actions or data retrieval occur. Once the tags pass the testing phase, they can be implemented throughout your security operations.
Introduce the NFC programable tags to your security guards and provide them with the necessary training. Explain the use cases, demonstrate how to interact with the tags using their NFC-enabled devices, and clarify any guidelines or protocols associated with their usage. Conduct regular training sessions to keep the guards updated on any changes or improvements related to the NFC tags.
Utilizing NFC programable tags in conjunction with security guard operations unlocks the potential for enhanced security and efficiency. By understanding the fundamentals of NFC technology, identifying relevant use cases, and leveraging TEKWave Solutions’ expertise, security guards can streamline their operations and improve overall security measures. Whether it’s tracking patrols, verifying checkpoints, accessing important information, or automating processes, NFC programable tags offer a versatile and effective solution. With TEKWave at the helm, providing innovative security solutions and a global presence, security can be taken to the next level. Contact TEKWave Solutions today to discover how their NFC-enabled solutions can transform your security operations and provide you with the TEKWave Advantage.
No related posts.